Learn about Cybersecurity best practices including how to deal with phishing messages, avoiding illegal file sharing, keeping your accounts safe, and more using the information below.
Phishing Scams
Don’t take the bait! Phishing attacks use malicious tactics to solicit personal information by posing as trustworthy entities to commit fraud.
Types of Phishing ScamsReceive a suspicious email? Forward it to abuse@uwm.edu.
Phishing attacks come in many forms. To learn about some of the most common types of scams, expand the sections below:
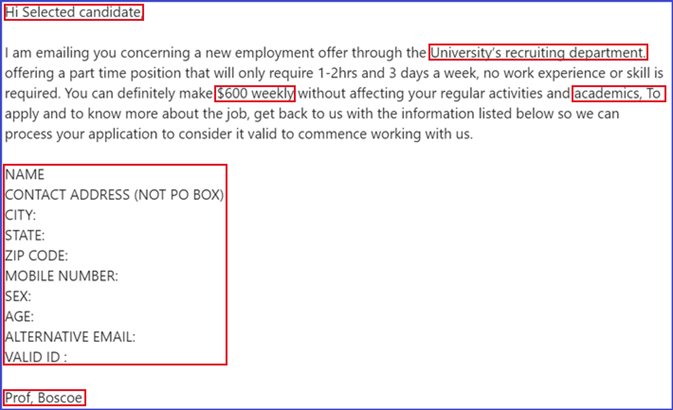
Job ScamsJob scams are enticing, fraudulent, messages used to gain access to sensitive information.
Job scam emails often come unexpectedly and advertise fake student job openings. These emails typically request the recipient respond to the email with specific information, click a link to fill out a form, or download an attachment, to apply. Often times job scams can be spotted simply by asking yourself “Is this too good to be true?”
Job Scam Red Flags:
- High weekly pay
- Low hours
- Lots of flexibility
- Requests for personal information
- Gender, social security number, passwords, phone number, etc.
- Email addresses from outside of UWM
- @gmail.com, @uwm.com, @uwm.org, etc.
- Vague university affiliation
- Short timelines
- Poor spelling or grammar
- Suspicious links or attachments
Looking for a legitimate job? Visit Handshake through the UWM Career Planning & Resource Center or contact them directly for other great opportunities!
Phone scams are fraudulent text messages (Smishing) or phone calls (Vishing) used to gain access to sensitive information.
Phone scams such as Vishing (scams that come in the form of a phone call) and Smshing (scams that come in the form of a text message) are almost always unexpected and often times scammers will use student loans, credit card debt, utility bills, account overdrafts, and other stressful topics to elicit a strong emotional response from their target. If you respond to one of these suspicious texts or engage in these calls, scammers will likely attempt to gather information from you such as credit card numbers, bank account numbers, MFA codes, and other identifying information.
Phone Scam Red Flags:
- Unknown numbers
- Urgent tone
- Short timelines
- Requests for personal information
- Passwords, age, MFA Codes, etc.
- Unsolicited calls/texts from authority figures or companies
- Utility companies, banks, the IRS, etc.
- Messages requesting you purchase gift cards
- Requests to click links in text messages
If someone asks you to pay for and share gift card details, it’s a scam.
Here is what to look out for with gift card scams:
- A scammer typically poses as someone you know, emails you to see if you are available and tells you it’s urgent.
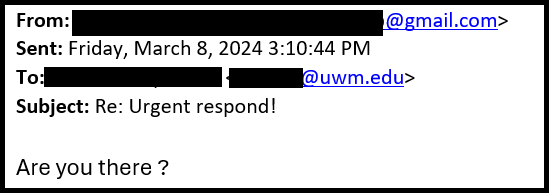
- After you respond, they ask you to go and buy a gift card, typically to a specific store, and promises that they will reimburse you.
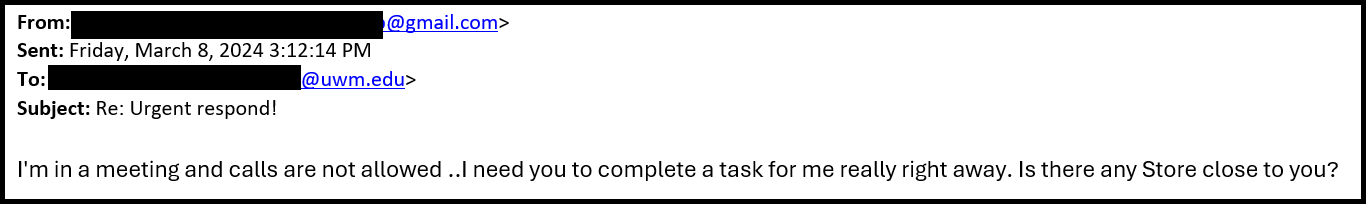
- Once you purchase the gift card, they will ask you to send them the gift card number and PIN, or a photo of the card.
What to do if you receive a gift card scam:
- Do not respond to these requests.
- If you believe you have received a gift card scam in your inbox, or are unsure, forward the email to UWM’s Information Security team at abuse@uwm.edu. This notifies our information security experts, and they can help you determine if the email is a scam.
- If you receive a gift card request from someone you know, contact them in an alternate way, and confirm if they sent the email.
- If you believe you have fallen victim to a gift card scam, please contact the UWM Help Desk.
For more information about gift card scams, check out this article from the Federal Trade Commission.
Security breach scams are fraudulent messages used to gain access to sensitive information.
Security breach scams use social engineering tactics to heighten their target’s anxiety to better their chances of stealing information. More often than not, these scams are seen in your inbox but can come via text and phone calls as well. Scammers state the victim’s account has been compromised and request for them to click links, download files, or respond with more information. Recently, these types of scams are used to try bypassing MFA.
Security Breach Scam Red Flags:
- Requests for personal information
- MFA codes, passwords, security questions, etc.
- Unofficial email addresses or addresses from outside the organization
- @uwm.com, @gma1l.com, @microsoft.org
- Unknown phone numbers
- Urgent tone
- Short timelines
- Requests to click links or download attachments
Cloud storage scams are fraudulent messages often used to extort money from victims.
Cloud storage scams attempt to extort money from targets using their personal files as leverage. For example, someone will message you claiming to have access to your cloud file storage account. The scammer proceeds to tell you that if they don’t receive a sum of money, then they will leak your account’s contents. Another popular tactic is where scammers will message you saying your account’s storage limit has been surpassed. After that, they will tell you to pay a certain amount otherwise your files will be deleted. In both cases, ensure you change your password immediately and contact your cloud storage provider.
Cloud Storage Scam Red Flags:
- Demands for money
- Vague language
- They don’t address you by name, they don’t share any information they have, they don’t mention the storage company, etc.
- Urgent tone
- Short timelines
- Messages from cloud storage systems you do not use
Customer service & social media scams are fraudulent messages used to gain access to sensitive information.
Customer service & social media scams weaponize established online profiles to commit fraud. By cloning notable figures, companies, and other accounts with large followings, fake accounts often ask their followers to click malicious links, divulge personal information, or pay a fee in exchange for various things. Common examples of these include job offers, unsolicited sweepstakes winnings, free gift cards, brand ambassadorship, shoutouts, and more.
Customer Service & Social Media Scam Red Flags:
- Unfamiliar, unverified, accounts
- Recently created accounts
- Little engagement on their profile
- Few followers
- Few posts
- Few likes
- Unsolicited messages
- Vague messages
- Urgent tone
- Short timelines
If you are ever unsure of an email’s legitimacy, forwarding it to abuse@uwm.edu notifies our information security experts and they can tell you if it’s a scam.
The Tell-Tale Signs of Phishing- Comes from an unknown email address/phone number
- Unsolicited job offers
- Requests for personal information
- Requests for immediate response
- Requests to click links
- Requests for attachment downloads
- Requests for MFA codes/approvals
- No personalization
- Vague university affiliation
If you believe you have received a phishing email:
- NEVER click any links or attachments
- Either click the ellipses (…) button in the upper right-hand corner and under Security Options select Mark as Phishing, or Delete the message
If you believe you are experiencing Vishing or Smishing:
- Do not respond to any text messages
- Do not click any links in text messages
- Delete any suspicious text messages
- Do not give out any personal information over the phone
- Hang up, contact the company directly using a verified communication channel listed on their official website or app, and ensure you are speaking to a legitimate company representative before discussing your issue.
- Block any and all suspicious numbers
To learn more ways to keep scammers at bay, visit our YouTube channel!
Data Security
Keeping your personal data secure doesn’t stop at your inbox! Learn about how to practice good data security in the following sections.
Virtual Private Networks (VPN)
Free WiFi may sound great in the moment, but if you're connecting to an unencrypted network, there's a good chance your personal data could be stolen if you aren't using a Virtual Private Network (VPN).
Does UWM have a free VPN for campus members?
UWM offers all campus members a free download of the Palo Alto VPN. Palo Alto provides encryption to UWM-provided products and services (e.g. PAWS, Canvas, M365, etc.) and the data you generate when using them. For instructions on how to download the Palo Alto VPN to your devices, visit our KnowledgeBase.
I want to encrypt all my traffic. What kind of VPN should I purchase?
Most VPN companies provide more than sufficient levels of security for all your devices, however; if you’re looking for specific recommendations, make sure the VPN provider you choose includes:
- AES128 (or better) level encryption
- IKEv2/IPSEC protocol
- Cross-platform compatibility
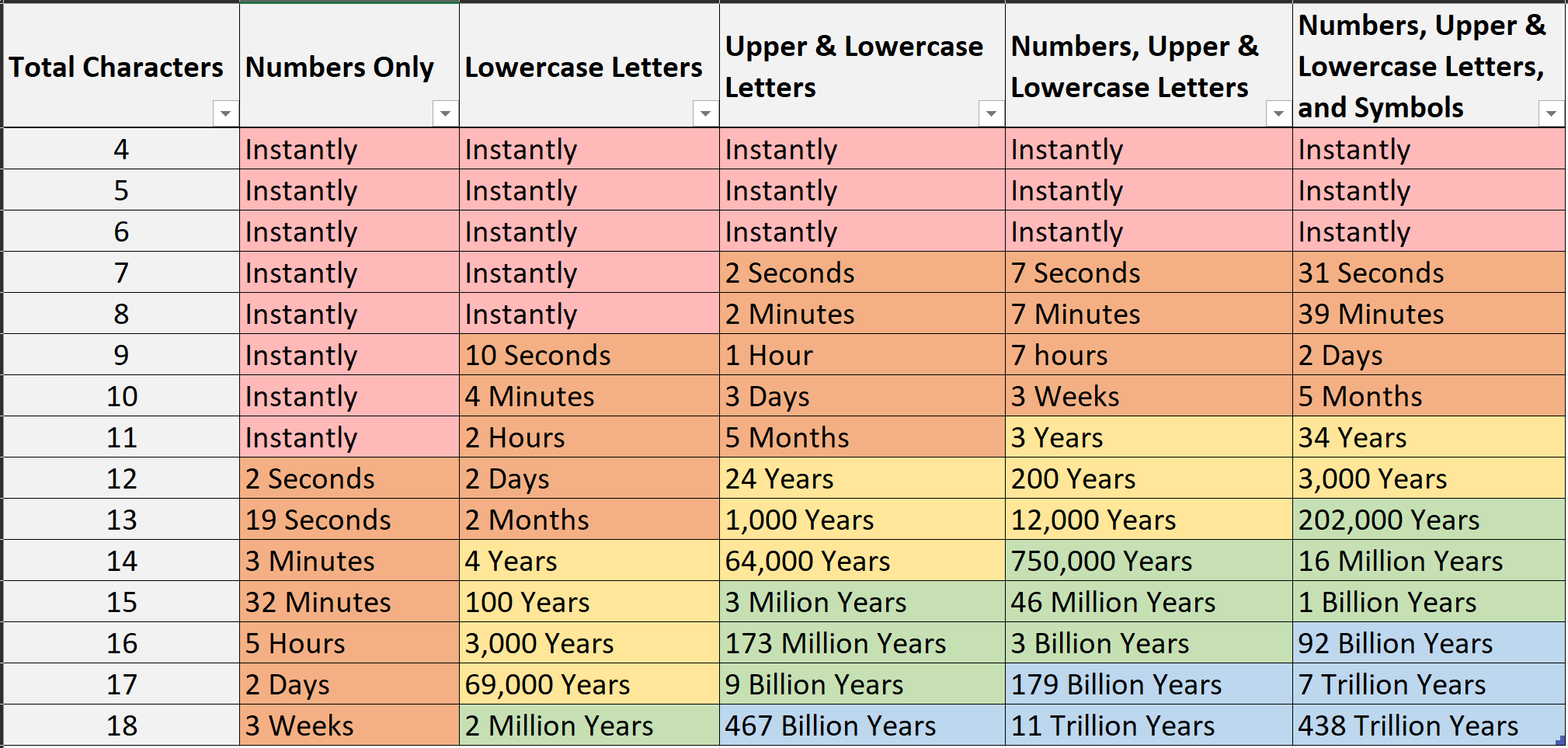
You may be wondering, “What? Passwords aren't good enough anymore?” Overall, passphrases contain more characters than a singular word and if someone were to try and “brute force” their way into your account, the chart below shows how long that would take.
Keep the following best practices in mind when making your next password:
- Use a phrase instead of a singular word (“makingapassword” vs “password”)
- Use uppercase and lowercase letters (Makingapassword)
- Use symbols (M@k!ng@P@$$Word)
- Use numbers (M@k1ng@P@55W0rd)
- Use as many characters as allowed
- Use a unique passphrase for each service you use
- Consider using a password manager so you don’t have to remember all of your unique passphrases
Please Note: Do not use the above password examples as your actual passphrase! (We know you’re smarter than that, but we still have to say it.)
Multi-Factor Authentication (MFA) adds an additional layer of security to the login process by requiring something you know (your password), to be used in conjunction with something you have (i.e. the Microsoft MFA App). This ensures your account stays safe even if someone steals your password.MFA @ UWM
Every UWM campus member uses Microsoft MFA to securely access their account. For more information regarding Multi-Factor Authentication, visit our resources:
MFA fatigue has become a popular tactic used by scammers when trying to gain access to your account. By bombarding you with frequent requests, the scammer hopes to get you to authenticate for them.
Some common ways they do this include:
- Lots of MFA requests coming one after another
- A few MFA requests each day for an extended period of time
- A person calls/texts you posing as a figure from a reputable institution that requests your MFA authentication as part of a company process
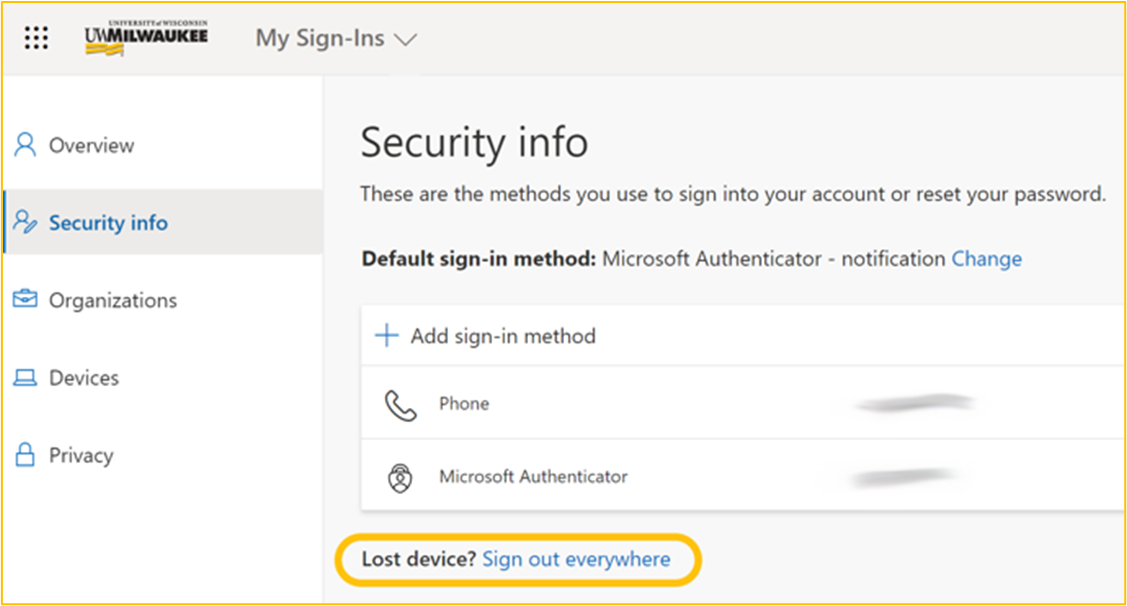
Think you’ve been MFA spammed? If you receive any unsolicited MFA prompts, all calls, texts, and emails should be handled carefully to ensure no one gains access to your personal information. To make sure no one gains access to your account:
- Turn off notifications for the authentication method being spammed.
- Immediately change your password.
- When logging into your account, use one of your backup methods to authenticate.
- Access your security info in M365, and select Sign out everywhere.
- Contact the UWM Help Desk to report the incident.

UWM IT recommends installing, updating, and regularly running antivirus software to protect your devices against virtual threats. Below are some suggested antivirus applications and resources meant for
personal devices.
Windows OS Antivirus SuggestionsAs of 12/19/2022, these are the recommended antivirus services for Windows devices:
- The Best Antivirus Protection
- The Best Free Antivirus Protection
- Microsoft Security Essentials (For Win7 and Older PCs, newer versions include Windows Defender by default)
As of 12/19/2022, these are the recommended antivirus services for Mac devices:
Most current-generation mobile devices come with antivirus software pre-installed, however; UWM IT recommends researching all applications you plan to download on your devices before accepting any user agreements.
Disclaimer: These recommendations are for personal devices. University-owned hardware should have antivirus software specific to UWM’s data protection needs already installed.
To report security-related issues, get help installing antivirus software, or receive help with other issues, contact the UWM Help Desk.

Knowing how to properly dispose of University-owned technology is essential to keeping your digital identity, and the work you do for UWM, secure. Please ensure you follow UWM IT's process for secure data disposal before sending your old computer to surplus.
To properly dispose of University-owned technology, please coordinate with Campus Technology Support (CTS) to ensure your old device is prepared for surplus. To do this, fill out the Request Help form and follow the instructions listed below:
- Under the My incident or request is related to… section, select Other
- In the Here is additional information about the request/problem… section, describe your secure data disposal needs
- Complete any other required fields and select Request Support to submit your request
After your request has been submitted, an IT professional will assess your device’s functionality, wipe its data, and remove it from UWM records.
After this has been completed, fill out the Surplus Declaration Form to coordinate your device’s pickup.
Request Secure Data Disposal through CTS
Making sure your computer is capable of running the latest safety features is essential to keeping yourself safe online. In addition, using certain physical barriers to keep yourself safe while in public and private settings can help enhance your cybersecurity.
The following hardware recommendations are meant to help enhance your cybersecurity and are not mandatory.
- Make sure your device adheres to UWM IT’s computer recommendations
- When your computer meets these specifications, it ensures you can receive any necessary security updates that can help protect you from the latest cyber threats.
- Put a webcam cover on your device
- Putting a webcam cover on your device ensures that your webcam cannot be used to watch you while you are not using it. Though this may sound intense, it has happened in the past, and the best way to keep others from doing it to you is to keep it covered when not in use.
- Put a privacy screen on your device
- Using something like a privacy screen makes it harder for people around you to see what you’re doing on your device. For example, if you have to log into your bank while you’re at a coffee shop, but don’t want people seeing your account balance, having a privacy cover over your screen can help keep your activity hidden from those around you.
Has your computer, account, server, or other technology been the victim of cybercrime?
Report your experience using our Cybersecurity Incident form.
Training Opportunities

Wanna get proactive about cybersecurity? We have training opportunities!
LinkedIn Learning
Learn about cybersecurity best practices using a self-guided LinkedIn Learning course! UWM IT recommends the following trainings for campus members:
- Internet Safety for Students (55 minutes)
- Cybersecurity at Work (55 minutes)
- Cybersecurity Foundations (120 minutes)
Learn a new skill in a TechTraining Short Course! Available online at the click of a button; learn how to securely save files, ensure you don’t lose important data, and keep yourself up to date with the latest best practices for applications.
Courses are free to attend and if you can’t make it to one, view a previous course on the UWM TechTraining website!
Check out UWM IT’s short-form video content on YouTube!
With topics ranging from how to get help with your technology all the way to how to set up Multi-Factor Authentication for your account, there’s something for everyone.
Illegal File-Sharing

There can be serious repercussions for Illegal File Sharing. Please review our Frequently Asked Questions below to get familiar with this important topic.DMCA & Illegal File Sharing FAQs
When media is produced and sold, it is protected by copyright law so it cannot be copied, reproduced, or resold without the permission of the creators. If you download media without paying for it and the file has been copyrighted, or distribute media that has been copyrighted without the permission of the copyright holder, you are sharing the file illegally. Make sure to always purchase media from a trusted outlet, and do not distribute copyrighted materials with others without permission from the copyright holder.
The Digital Millennium Copyright Act (DMCA) of 1998 made it illegal to republish copyrighted information by downloading, uploading, or file-sharing media such as music, movies, or software. Digitally sharing copyrighted materials is illegal and violates the Acceptable Use Policy for UWM regarding the campus network.
The University does not monitor individual network activity. However, UWM is obligated by law to respond to valid complaints from copyright holders and their agents. DMCA complaints are taken seriously and may result in loss of access to the UWM network, academic discipline under University policy, or fines or legal action by the copyright holders and/or their agents.
Groups like the Recording Industry Association of America (RIAA) pay organizations to gather information from the internet to identify where files are being shared illegally. Individual lawsuits are being settled out of court for $4,000-$5,000. Lawsuits that are not settled out of court can result in higher monetary damages.
Groups such as the RIAA send an official complaint to the Internet Service Provider (UWM when you are using the UWM network). UWM notifies the campus network administrator responsible for the area in which the infringement occurred. The individual is then notified about the complaint so they can stop the illegal use of copyrighted material. Wherever possible, network access for the device or individual in question is removed until it can be verified that the infringing activity has stopped or until a counterclaim is filed.
The copyright holders’ lawyers can file a federal lawsuit and then subpoena the University for the information to identify the individual. With your name and user account information, the attorneys can pursue monetary damages against you in court. This is the risk you assume when you engage in illegal file sharing.
The use of programs such as BitTorrent, uTorrent, and LimeWire may result in illegal P2P sharing of digital materials.
While some files may be legally shared via common P2P programs, most true freeware programs or public domain music are available elsewhere on the Internet. If you use P2P file sharing software, it is your responsibility to ensure you are not downloading or sharing copyrighted music, movies, or software.
If you’ve been contacted regarding a DMCA violation, you may have been targeted for the settlement letter as well. If you wish to obtain a copy of any such letter or contact information for the RIAA, you may request it from UWM. Incidentally, the parties to a lawsuit can agree to settle a case at any time. You do not legally forfeit your right to settle by not responding to a pre-settlement letter. While it is impossible to know if the RIAA will be amenable to settlement at a particular time in the future, typically corporations prefer to settle cases instead of undertaking a trial which is costly and time-consuming.
It is the policy of the University of Wisconsin – Milwaukee (‘UWM”) to promptly investigate notices of alleged copyright infringement, and take appropriate actions under the Digital Millennium Copyright Act, Title 17, United States Code, Section 512 (“DMCA”).
DMCA notifications are to be submitted to the DMCA Compliance and Notification Agent.